
02: Security Operations and Frameworks¶
In this session we will cover:
- Operational Overview and the role of the SOC
- Analytical Workflow (MAPE-K)
- Security Frameworks
Operational Overview¶
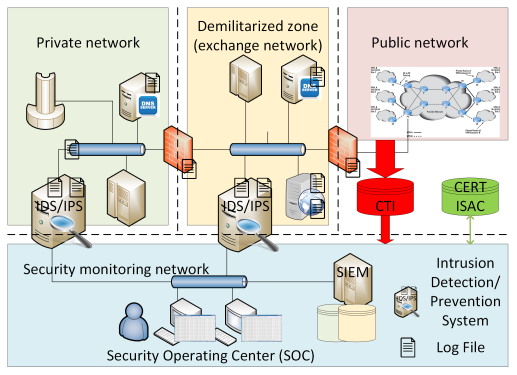
Operational Architecture: Think about how the SOC interacts with the various different security zones
- SOC needs security intelligence about internal networks, and cyber threat intelligence (CTI) about external public networks, as well as Information Sharing and Analysis Centers (ISACs) and Computer Emergency and Response Teams (CERT).

- Security Operations Centre (SOC): Centralized security monitoring and incident response within an organization - employing people, processes, and technology to continuously monitor and improve an organization's security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
- Data is gathered in the form of logs: event logs, application logs, system logs, network traffic logs, user logs, etc.
- We may examine logs as raw files (e.g., PCAP) or we may ingest these within a Security Information and Event Management (SIEM) system.
Monitor, Analyse, Process, Execute - Knowledge (MAPE-K)¶
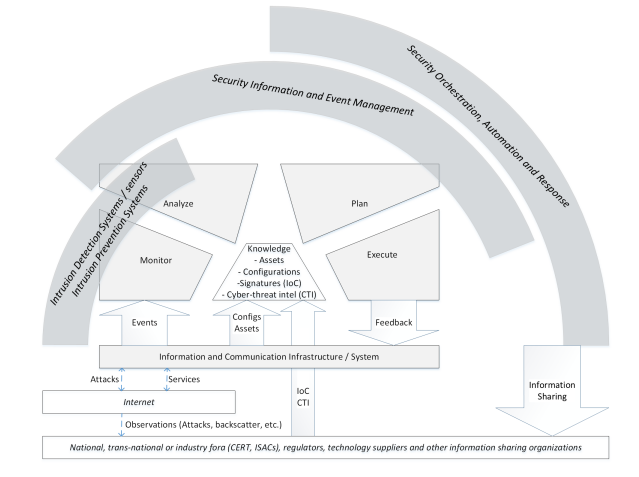
The MAPE cycle aids the development of knowledge - previous security measures have sought to address this cycle.
- IDS/IPS: Traditional security that covers monitoring and analysis.
- SIEM: Broader capability and data ingest that extends to planning/decision making.
- SOAR: Like above, but with additional automated response capabilities.
Monitor Phase (Data Collection)¶
- Network traffic: Full packet capture (PCAP) of the network - widely used due to the reliance on networking.
- Network aggregation: Where full PCAP is impractical, concepts such as Netflow represent communications by aggregating data into communication flows.
- Network infrastructure: Naming and routing data is crucial to ensure the network is operating as intended - Domain Name System (DNS) and BGP (Border Gateway Protocol).
- Application logs: Web server logs, and application files/documents.
- System logs: Syslog protocol can be used to capture important system event logs.
Analysis Phase¶
- "An Intrusion Detection model" by Denning dates back to 1987.
- Misuse detection: Can we detect when something is a 'known bad'? Signature-based methods such as Snort rules for IDS/IPS, and Anti-virus definitions work in this manner.
- Anomaly detection: Can we detect when something is different from a 'known good'? Harder to qualify why something is therefore bad. Can use statistical methods or machine learning approaches to model the problem.
- Typical security analysts aims to classify good/bad activity, or perform a multi-class classification of some data observations (e.g., malware families, user profiles).
- Security Information and Event Management (SIEM) tools offer integrated data ingest and data storage with statistical analysis and machine learning analysis techniques.
Planning Phase¶
- SIEMs act as decision support systems - how do analysts decide if action is required?
- Data collection and aggregation, coupled with 'rules' or 'playbooks' to best guide decision-making. More...
- Alert correlation: Reasoning about multiple data observations, and whether a relationship exists.
- Correlation between similar alerts
- Correlation between alerts and the environment
- Correlation between alerts and external sources
- Incident and information exchange
Always remember: Correlation does not imply causation
Execute Phase¶
- Traditionally a manual process, however automation is slowly being adopted in part (cautiously!).
- IPS detects and responds to threats - but what about false positive/false negative cases?
- DoS mitigation - automation helps to react in time.
- SOAR yet to be mainstream - cost/benefit/risk - research address best practice for *human-machine collaboration*.
Data Science Workflows¶



Security Operations and Incident Management is essentially a subset of Data Science.¶
*Analytical reasoning* about *data observations* to inform on *cyber risk* to our organisation
Security Frameworks and Knowledge bases¶
Cyber Kill Chain¶
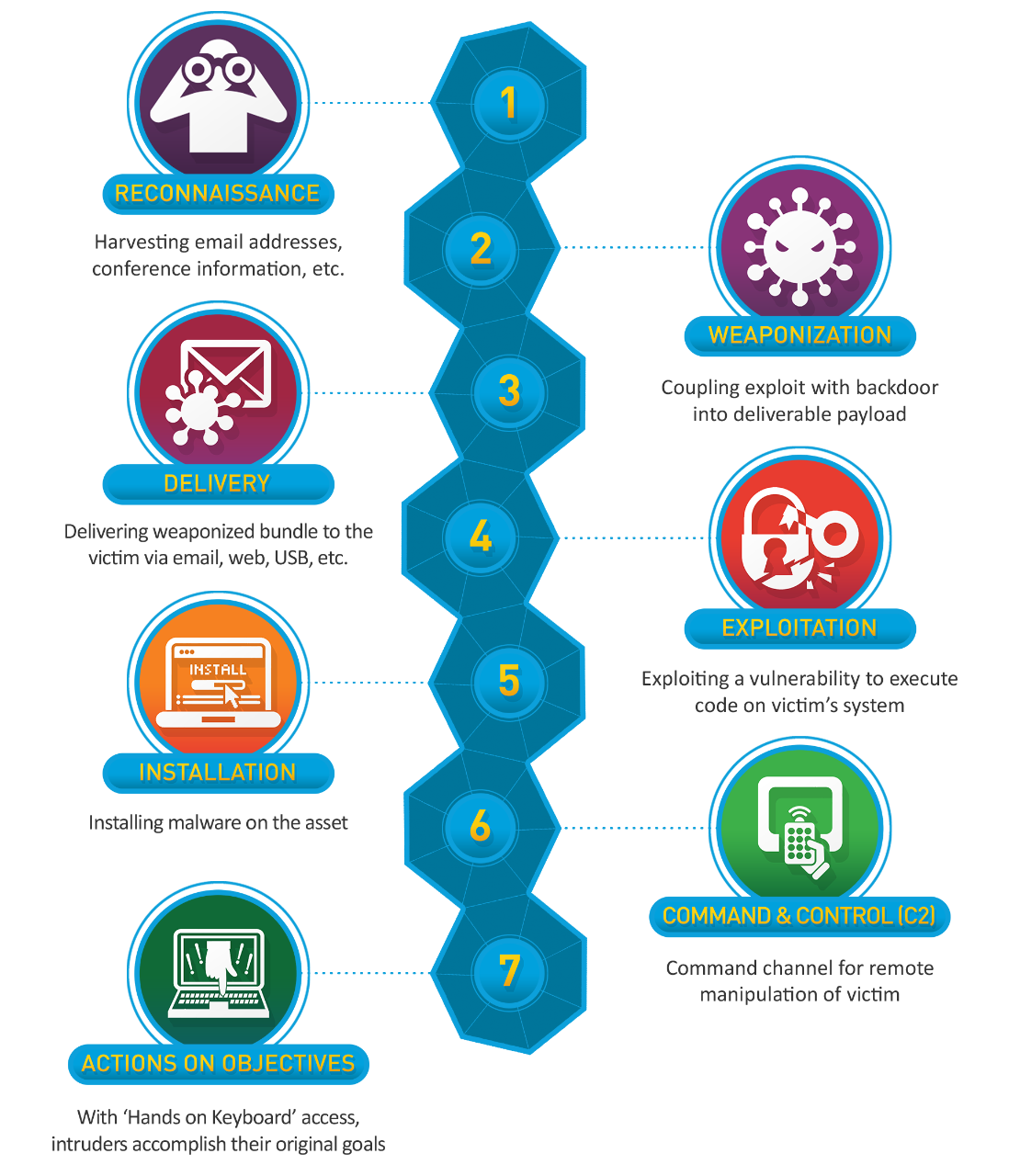
The Lockheed Martin Cyber Kill Chain framework helps the identification and prevention of cyber intrusions activity. The model identifies what the adversaries must complete in order to achieve their objective. The seven steps of the Cyber Kill Chain enhance visibility into an attack and enrich an analyst’s understanding of an adversary’s tactics, techniques and procedures.
MITRE ATT&CK¶
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a knowledge base of adversary tactics and techniques based on real-world observations. Created in 2013, researchers emulated both adversary and defender behavior to improve post-compromise detection and analysis. Framework based on Tactics, Techniques and Procedures (TTPs).
Tactics: Reconnaissance / Resource Development / Initial Access / Execution / Persistence / Privilege Escalation / Defense Evasion / Credential Access / Discovery / Lateral Movement / Collection / Command and Control / Exfiltration / Impact.
Techniques listed for each Tactic.
Procedures given for each Technique.
How Useful is MITRE ATT&CK Framework in Threat Intelligence?
Common Vulnerabilities and Exposures (CVE)¶
The Common Vulnerabilities and Exposures programs aims to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. There is one CVE Record for each vulnerability in the catalog used as a global identifier. Partners publish CVE Records to communicate consistent descriptions of vulnerabilities. Information technology and cybersecurity professionals use CVE Records to ensure they are discussing the same issue, and to coordinate their efforts to prioritize and address the vulnerabilities. In the United States, the National Institute of Science and Technology (NIST) maintain a National Vulnerability Database (NVD) that references against the catalogued CVE database.
- CVE-2014-0160: Heartbleed
- CVE-2017-0144: WannaCry
- CVE-2020-10148: SolarWinds Orion
- CVE-2021-44228: Apache log4j
MITRE Cyber Analytics Repository¶
The MITRE Cyber Analytics Repository (CAR) is a knowledge base of analytics developed by MITRE based on the MITRE ATT&CK adversary model. CAR defines a data model that is leveraged in its pseudocode representations, but also includes implementations directly targeted at specific tools (e.g., Splunk, EQL) in its analytics. With respect to coverage, CAR is focused on providing a set of validated and well-explained analytics, in particular with regards to their operating theory and rationale.
Analytics stored in CAR contain the following information:
- a hypothesis which explains the idea behind the analytic
- the information domain or the primary domain the analytic is designed to operate within (e.g. host, network, process, external)
- references to ATT&CK Techniques and Tactics that the analytic detects
- the Glossary
- a pseudocode description of how the analytic might be implemented
- a unit test which can be run to trigger the analytic
Further reading¶
Practical Session¶
- Continue to explore the lab examples:
- 00-Python Primer
- 01-"Hello, Security Analytics"
- 02-Network Traffic Analysis
- Dig deeper into using Pandas for Python data analysis
- Portfolio Task 1 - see Blackboard.

