About Me¶

Professor in Cyber Security
Co-Director: UWEcyber ACE-CSE
Programme Leader: BSc Cyber Security and Digital Forensics (2024-); MSc Cyber Security (2018-24)
Module Leader: Cyber Security Analytics (2021-); Security Data Analytics and Visualisation (2017-24)
Research: Cyber Security, Machine learning, Visualisation - insider threat, security analytics, adversarial AI, explainable AI
4Q59 / Phil.Legg@uwe.ac.uk / plegg.me.uk / @ProfLegg
Module Information¶
Assignment¶
This module is assessed by a portfolio that is worth 100% of the marks.
- Task 1 (Week 2 discussion): Practical coding task on Data Science for Cyber Security.
- Task 2 (Week 4 discussion): Practical coding task on Machine Learning for Cyber Security.
- Task 3 (Week 6 discussion): Practical research task on Security Data Analytics.
Submission date: Thursday 1st May 2025 @ 14:00 (48-hour late window applies).
Submissions are to be made via Blackboard.
Please see Blackboard for further details.
Module Overview (Weeks 1-6)¶
- Introduction / Role of Cyber Security Analytics
- Security Operations and Frameworks (Task 1 Release)
- Security Monitoring and Analysis
- Machine Learning for Cyber Security (Task 2 Release)
- Visualisation for Cyber Security
- Mid-module review / Recap of Tasks (Task 3 Release)
Schedule is subject to change, please follow Blackboard announcements.
Module Overview (Weeks 7-12)¶
- Case Studies: Malware Analysis / Cyber Security Analytics Research
- Case Studies: Insider Threat Detection
- Case Studies: Text Analytics
- Future of Cyber Security Analytics / Module Recap (Assignment Submission)
- Additional support
Schedule is subject to change, please follow Blackboard announcements.
Feedback¶
- Please make use of the online Q&A form to post your course questions (also linked on Blackboard).
- I will collate and respond to these questions via course announcements so that all students can benefit by the response.
- Please do regularly check your emails to observe course annoucements.
- Please do continue to work on tasks outside of sessions so that you bring questions to the lab sessions.
- Please work through the non-assessed labs - they will help you with the assessed labs!
- You will receive formative feedback on your work during lab sessions, please use this to develop your final submissions.
- You will receive summative feedback at the end of the course on return of your assignments.
Other useful resources¶
- CyBOK: Security Operations and Incident Response
- CyBOK: Malware and Attack Technologies
- This course is aligned to these two CyBOK Knowledge Areas.
- Certification: CompTIA Cybersecurity Analyst (CySA+)
- This course covers many of the topics related to this industry certification.
- Employability: UK Cyber Security Council
- This resources covers career paths that align with the skills developed in this modules.
01: Role of Cyber Security Analytics¶
In this session we will cover:
- What is the role of a Cyber Security Analyst?
- Roles, responsibilities, skills required, job opportunities
- Why is Data Science important to Cyber Security?
- What kind of tools exist to integrate Data Science and Cyber Security?
What is the role of a Cyber Security Analyst?¶
What do you think Cyber Security Analytics is all about?¶


- Understanding data related to your organisational security
- Developing situational awareness: past, present and future
- Identifying and responding to threats

- Network traffic
- System logs
- Application data
- Email activity
- Reputation / threat database - blacklists of known threats
- Open-Source Intelligence (OSINT)
"Cyber Security Analytics is about how data can be used to inform of threats, vulnerabilities and risk that an organisation may be exposed to."¶
It is a defensive strategy to better understand the operational environment of digital assets, and a means to make better informed decisions to protect and defend the organisation.
Cyber Security job roles¶
Entry level¶
- Cyber security analyst
- Cyber security specialist / technician
- Cyber crime analyst / investigator
- Incident analyst / responder
- IT auditor
Mid level¶
- Cybersecurity analyst
- Cybersecurity consultant
- Penetration and vulnerabilitiy tester
Advanced level¶
- Cybersecurity manager / administrator
- Cybersecurity engineer
- Cybersecurity architect
Job Opportunities¶
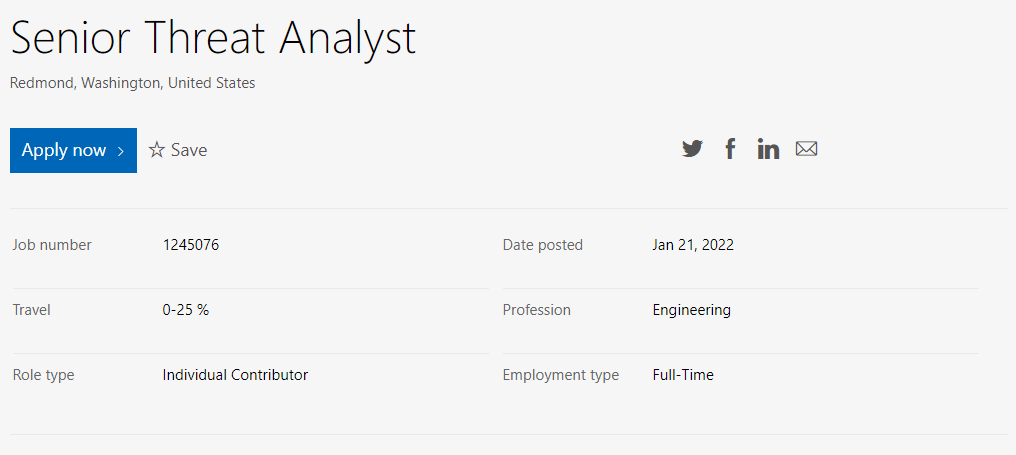
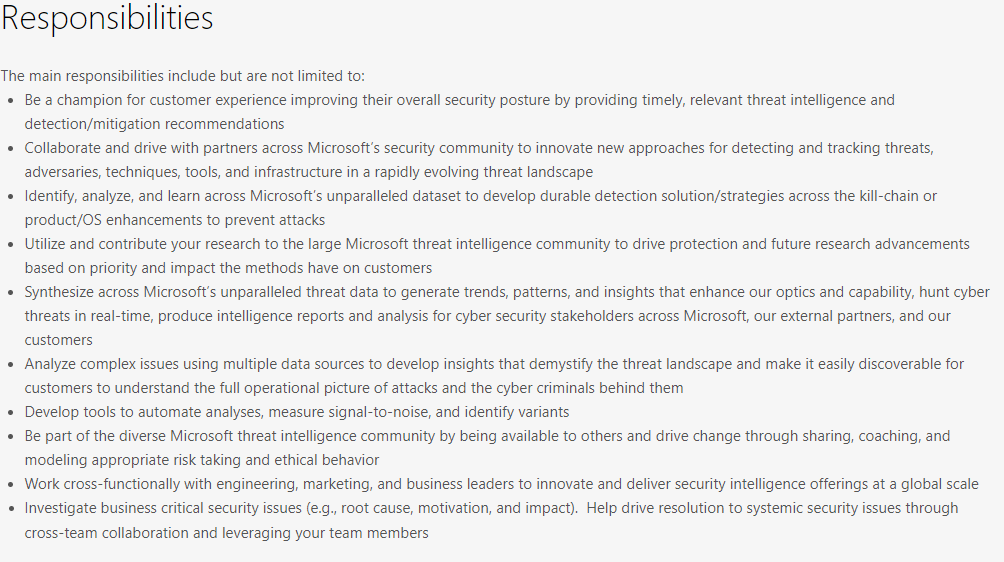
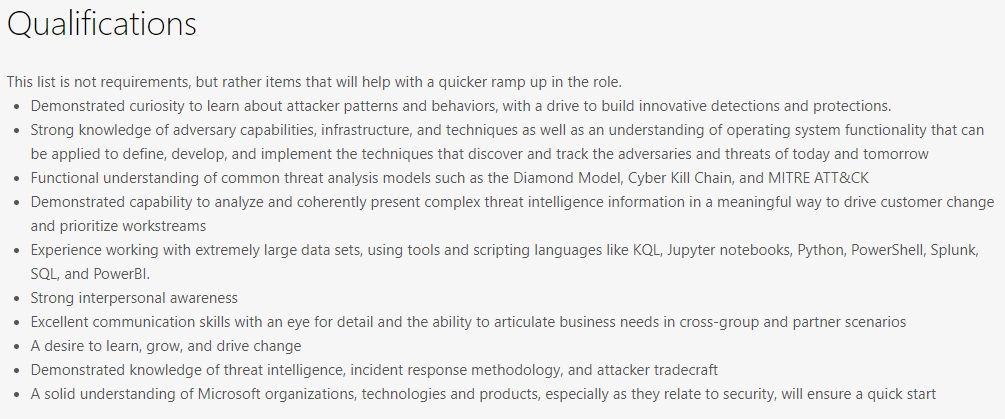
Security Intelligence is a process¶
- Requirements (Planning and Direction)
- Collection (and processing) - SIEMs
- Analysis - ML, AI, data science - all analysis done in the context of a user case developed in the planning stage.
- Dissemination
- Feedback
Security Intelligence vs Cyber Threat Intelligence¶
- Security intelligence tends to be an inward facing activity - internal observations in our logs.
- Cyber threat intelligence tends to be an outward facing activity - external threats that we need to prepare for.
Are we dealing with narrative reports or with data feeds? We need to consider both!
Network Security Tools¶
- Network traffic data (e.g., packet captures) can be used to identify what information has been communicated, and therefore what activity has taken place on a network (e.g., access to a particular URL, or downloading of particular files).
- Firewalls can be used to block inbound/outbound activity based on pre-configured rules (e.g., IP address, port number, etc...).
- Intrusion Detection Systems (IDS) inspect inbound/outbound network traffic to identify suspicious activity.
- Intrusion Prevention Systems (IPS) inspect inbound/outbound network traffic to identify suspicious activity and automatically block.
Big Data Security Analytics¶
“Security is about understanding systems, the people, and the processes that act upon these systems, such that they remain secure”
Security Data Visualization Skills¶
Data science and security visualisation requires the following blend of skills that combines the ability to hack and manipulate data, the understanding of statistical techniques, and the domain knowledge of what information is relevant and important for the purpose of security.
- Substantive Expertise – This is the security domain knowledge, which will enable the security practitioner to understand the data, determine what is expected and find anomalies or metrics from visualization.
- Hacking Skills – Hacking skills are the skills from a data scientist language required for working with massive amount of data that should be acquired, cleaned and sanitized.
- Math & Statistics Knowledge – This knowledge is critical to understand which tools to use, understand the spread and other characteristics to derive insight from the data.
Data-Driven Storytelling¶
- Novelty: We may want to observe when something is new within our observation.
- Outlier: We may want to observe when something not new appears different within our observation.
- Trend: We may want to observe the historical pattern of observations.
- Forecasting: We may want to observe how the historical pattern will forecast what may come in the future.
- Debunking: We may want to observe how our data contradicts an opinion of what may come.
Practical Session¶
- Get started with the UWEcyber Virtual Machine
- Use the JupyterLab environment to learn about Python notebooks.
- Complete the non-assessed lab exercises to develop your Python skills:
- 00-Python Primer
- 01-"Hello, Security Analytics"
- 02-Network Traffic Analysis
